Which of the Following Best Describes an Email Security Gateway
The server that he cannot remotely access to is located on. Solutions for Chapter 2B Problem 14MCQ.

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security
The proxy server is also called application level gateway.

. Internet and Email MCQs is the set of important MCQs on Internet and Email covering the frequently asked questions in the past papers of different admission test job test and public service commission tests. Do you want to create a DMZ for these two servers. Of the following security security zones which one can serve as a buffer network a private secured network and the untrusted internet.
Which of the following are functions of gateway email spam blockers Select Two A. Which of the following best describes a major security issue when implementing WAPs. A security analyst has discovered suspicious traffic and determined a host is connecting to a known malicious website.
Email -- but not email security -- protocols. A white-hat hacker is a good guy who uses his skills for defensive purposes. It is therefore imperative that every organizations security strategy include a robust email security solution.
What is ARP Spoofing ARP Poisoning An ARP spoofing also known as ARP poisoning is a Man in the Middle MitM attack that allows attackers to intercept communication between network devices. The SSID is broadcast in plain text. Configure the firewall to block traffic to the domain.
The MOST appropriate action for the analyst to take would be lo implement a change request to. Update the antivirus software. Michael is a system administrator who is troubleshooting an issue with remotely accessing a new server on the local area network.
The following control how email is transmitted formatted and retrieved. They scan the network to determine the IP addresses of at least two devices. Your company has a connection to the Internet that allows users to access the Internet you also have a Web server and an email server that you want to make available to the Internet users.
Wi-fi protected access wired. Simple Mail Transfer Protocol SMTP specifies how messages are transmitted. The attacker must have access to the network.
Firewall management lets you monitor and configure Sophos Firewall devices that you connect to Sophos Central. By this the client computer can establish indirect network connection to. All email security gateways have the ability to quarantine or block email that contains detected malware phishing attacks spam as well as other malicious contentThis prevents most attacks from reaching their intended recipients which in turn reduces the number of successful compromises of hosts user credentials and sensitive data.
Which of the following statements best describes a white-hat hacker. Because attacks are increasingly sophisticated standard security measures such as blocking known bad file attachments are no longer. Email Security provides protection against spam spoofing and viruses.
An email directing the recipient to enter personal details on a fake website An email warning the recipient of a computer virus threat An email advertyising a department store An unwanted email that installs a virus on the recipeints computer A 45 What is WPA. The attack works as follows. 44 Which one fo the following best describes phishing.
He is using an LMHOST file which contains the hostname and IP address of the new server. Enable in transport encryption protection to. ASending multiple spoofed ICMP packets to the victim.
Which of the following best describes an exclusive gatewaya. They are hard to physically locate. One of the first best practices that organizations should put into effect is implementing a secure email gateway.
A with external access. The analyst is given the following requirements. Sophos Web Gateway protects your network against risky or inappropriate web browsing.
A gateway with only one exit path per instance of a processd. An email gateway scans and processes all incoming and outgoing email and makes sure that threats are not allowed in. A gateway that does not connect to message flowsc.
A proxy server is a computer that acts as a gateway between a users computer and the Internet. Whether its sophisticated nation-state attacks targeted phishing schemes business email compromise or a ransomware attacks such attacks are on the rise at an alarming rate and are also increasing in their sophistication. Which of the following best describes the ping of death.
The only gateway in a BPMN diagramb. Basic insecure email depends on just a handful of protocols. CompTIA JK0-801 A Networking PC Hardware Practice Exam Set 6.
Former grey hat D. A companys Chief Information Security Officer CISO recently warned the security manager that the companys Chief Executive Officer CEO is planning to publish a controversial option article in a national newspaper which may result in new cyberattacks Which of the following would be BEST for the security manager to use in a threat mode. Former black hat C.
Preserve the use of public IP addresses assigned to equipment on the core router. A security analyst is hardening a network infrastructure. A security audit performed on the internal network.
A security administrator would like to increase the security of the companys email. WEP is the default encryption. The Internet service that issue a multimedia interface to current resources is called.
Which of the following BEST describes the environment that the network administrator will. It is important to note that these are not email security protocols. Malicious hacker Answer 1.
Any node can view the data of another. A gateway where all exit paths are taken for each instance of a processe.
Installing And Configuring Endpoint Security Url Filtering
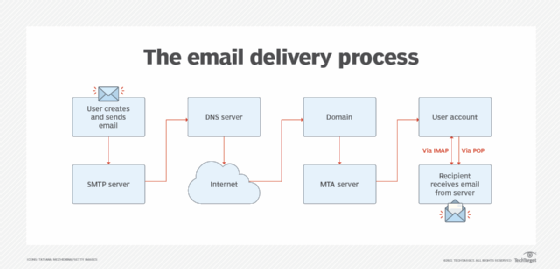
What Is Imap Internet Message Access Protocol

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security

Modules 1 4 Securing Networks Group Exam Answers Full

Configure Proofpoint Email Protection With Exchange Online Exchange Microsoft Docs
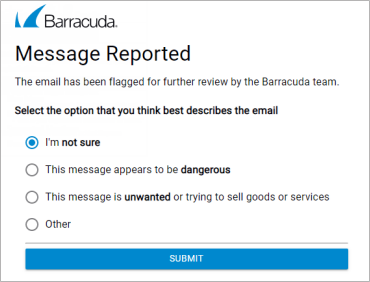
Barracuda Essentials For Email Security Outlook Add In User Guide Barracuda Campus

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security
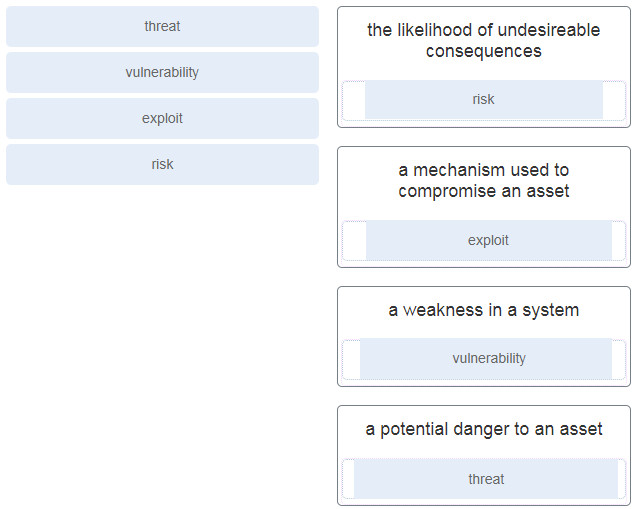
Modules 1 4 Securing Networks Group Exam Answers Full

Ccna Cybersecurity Operations Version 1 1 Cyberops Chapter 10 Exam Answers 2019 Premium It Exam Answers

Key Findings The Forrester Wave Enterprise Email Security Q2 2019

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security
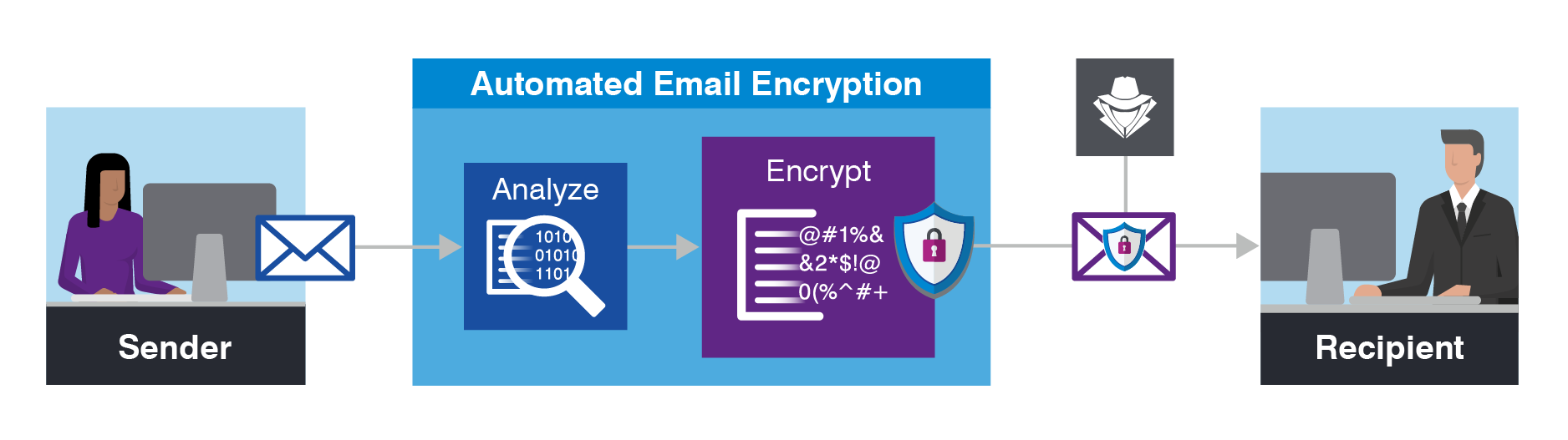
What Is Email Security Meaning Best Practices More Proofpoint Uk
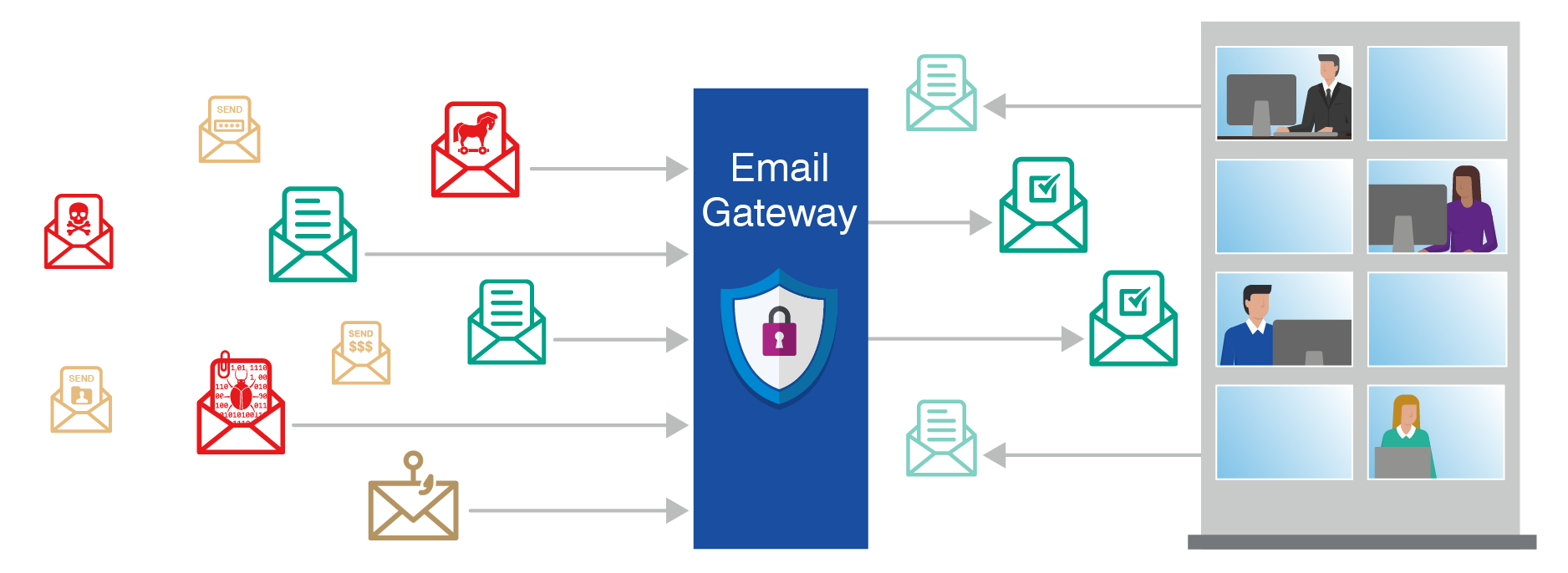
What Is Email Security Meaning Best Practices More Proofpoint Uk

Comments
Post a Comment